Having your private images or intimate videos shared online without consent is one of the most traumatic digital violations a person can experience.
It can feel overwhelming, humiliating, frightening, and hopeless—especially when the internet feels permanent. Many victims blame themselves. Many stay silent. Many don’t know where to start.
Let’s be very clear first:
Non-Consensual Intimate Imagery (NCII) is abuse.
It is not your fault.
And there are ways to fight back and regain control—within realistic limits.

This guide is written to be empathetic, practical, legally accurate, and brutally honest. No fake promises. No “everything can be erased” myths. Just real tools, real steps, real limitations, and real hope.
What Is NCII (Non-Consensual Intimate Imagery)?
NCII refers to:
- Intimate photos or videos
- Shared without your consent
- Often after a breakup, hack, coercion, or extortion
It includes:
- “Revenge porn”
- Leaked MMS
- Private videos uploaded to porn sites
- Images shared on Telegram, WhatsApp, Discord, Reddit, Twitter/X
- Content used for blackmail or sextortion
NCII is recognized globally as a serious violation of privacy and dignity, and in many countries, it is a criminal offense.
First: What You Should (and Should NOT) Do Immediately
✅ What You SHOULD Do
- Stay calm (panic leads to mistakes)
- Preserve evidence (screenshots, URLs, timestamps)
- Act fast on major platforms
- Seek help (you don’t need to do this alone)
❌ What You Should NOT Do
- Don’t pay blackmailers (they almost never stop)
- Don’t threaten impulsively
- Don’t assume reporting once is enough
- Don’t believe “nothing can be done”
Step 1: Use Dedicated NCII Removal Tools (Most Powerful)

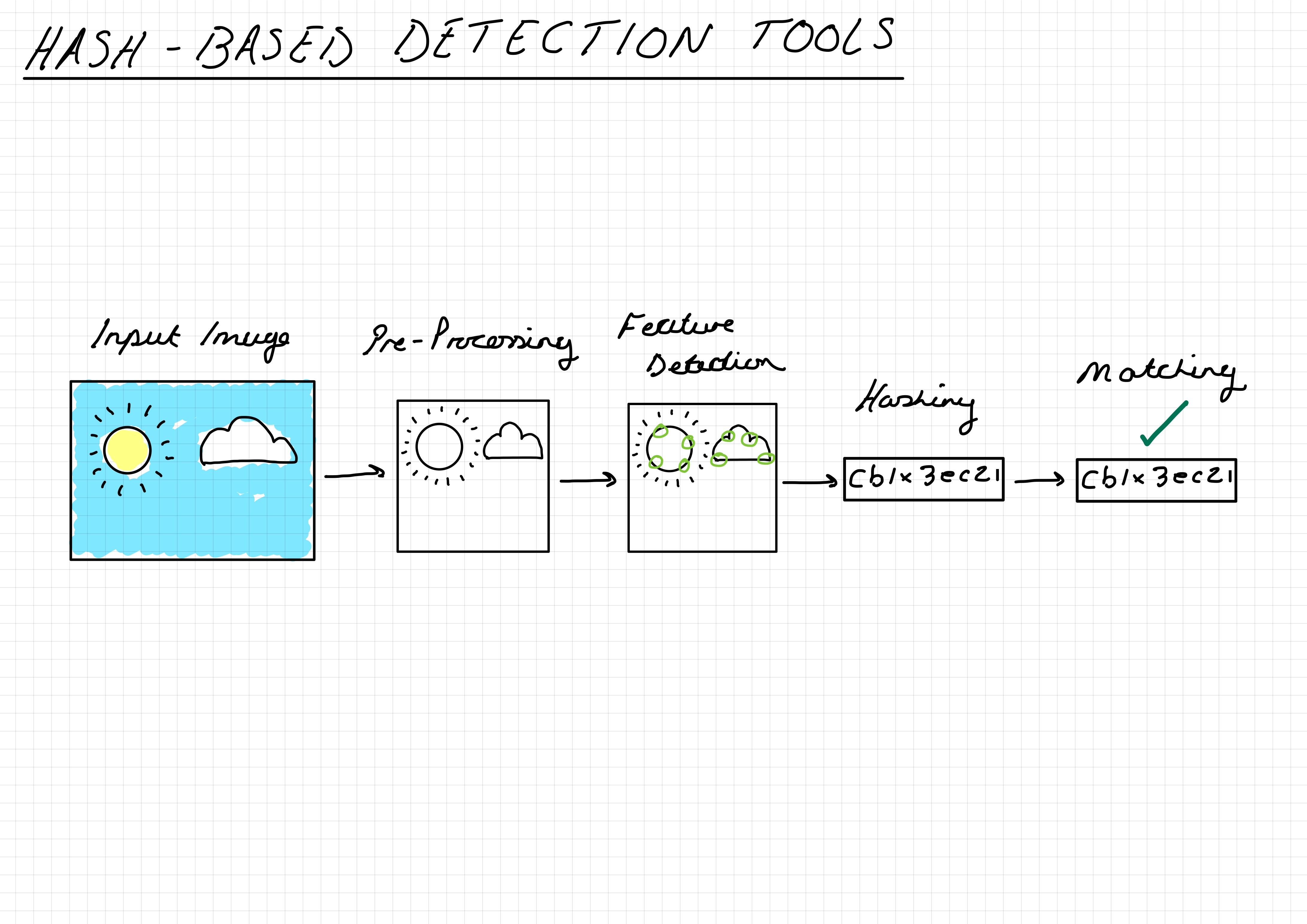
🔹 StopNCII.org (Highly Recommended)
If you are 18+ and have the original image or video, this is one of the strongest tools available today.
How StopNCII Works (Important to Understand)
- Your image/video never leaves your device
- A digital fingerprint (hash) is created locally
- That hash is shared with participating platforms
- Platforms scan uploads and block/remove matches
Participating platforms include:
- Meta (Facebook, Instagram)
- TikTok
- Snap Inc. (Snapchat)
Why This Matters
- Prevents future re-uploads
- Protects even if someone tries again
- Does NOT expose your content to moderators
✔ Privacy-preserving
✔ Free
✔ Victim-centric
Step 2: Report Directly on Platforms (Manual but Necessary)
Every major platform has NCII-specific reporting flows.
Common Platforms to Report On
- Instagram / Facebook
- X (Twitter)
- Telegram
- Discord
- Pornographic websites
What to Include in Reports
- Clear statement: “Non-consensual intimate content”
- Proof of identity (if requested)
- URLs of the content
- Screenshots
- Statement of lack of consent
Pro tip: Use calm, factual language. Emotional messages slow moderation.
Step 3: Remove It From Search Engines (Critical for Visibility Control)


Even after removal, search engines may still show links or previews.
🔹 Google Personal Content Removal
Google allows you to request removal of:
- Explicit images/videos
- Content shared without consent
- Outdated cached previews
This does not delete the content from the internet—but it dramatically reduces discovery.
Why This Step Is Crucial
- Stops strangers from finding it
- Protects your name & reputation
- Reduces long-term damage
Step 4: DMCA Takedowns (If You Own the Content)
If you created the image or video, you likely hold the copyright.
What Is a DMCA Takedown?
A legal request demanding removal of copyrighted content.
Where DMCA Works Well
- Websites
- Hosting providers
- Adult platforms
- File-sharing sites
Limitations
- Doesn’t work if someone else created the content
- Some rogue sites ignore DMCA
- Needs repeated submissions
Still, it’s a powerful legal tool.
Step 5: Law Enforcement & Legal Action (When to Escalate)
When to Consider This
- Ongoing harassment
- Sextortion
- Threats
- Distribution at scale
- Minor involved (urgent)
Many countries now classify NCII as a criminal offense.
Legal Help Can:
- Force takedowns
- Identify perpetrators
- Support restraining orders
- Strengthen platform cooperation
Even filing a report creates an official record, which helps later.
The Hard Truth: Limitations You Must Understand
This part matters the most.
❗ The Internet Cannot Be “Fully Erased”
Let’s be honest.
1. Edited or Altered Versions
If someone:
- Crops
- Adds filters
- Overlays text
- Re-encodes video
Hash-based systems may not detect it.
Each variation may require separate reporting.
2. Non-Participating Platforms
Some sites:
- Don’t cooperate
- Are hosted offshore
- Ignore abuse complaints
These require manual + legal pressure.
3. Encrypted Messaging Apps
Platforms like:
- Signal
- Private Telegram chats
Content here cannot be scanned or removed externally.
4. Offline Copies
Once someone downloads your content:
- No tool can delete files from their device
- Prevention becomes the focus, not deletion
This is painful—but understanding it prevents false hope.
What “Control” Actually Means (Realistic Definition)
You may not erase every copy.
But you can:
- Remove it from public platforms
- Block future uploads
- De-index it from search engines
- Reduce visibility to near zero
- Protect your identity going forward
For most victims, visibility reduction is the biggest relief.
Emotional & Psychological Impact (Often Ignored)
NCII causes:
- Anxiety
- Depression
- Fear
- Social withdrawal
- PTSD-like symptoms
Seeking help is not weakness.
Consider:
- Trusted friends
- Support organizations
- Mental health professionals
Your well-being matters more than pixels online.
Long-Term Protection Strategies
Digital Hygiene
- Lock down social media privacy
- Remove personal info from public sites
- Use strong passwords + 2FA
Reputation Repair
- Create positive content under your name
- Control search results over time
- Don’t disappear—strategic presence helps
Myths You Should Stop Believing
❌ “Once online, forever online”
➡ Visibility can be drastically reduced
❌ “Reporting doesn’t work”
➡ It does—when done properly and persistently
❌ “It’s my fault”
➡ It is never your fault
Final Words (Please Read)
If you are dealing with leaked intimate content, remember this:
- You are not alone
- You are not powerless
- You deserve dignity and control
- The internet does not define your worth
Taking action—step by step—does make a difference.
Frequently Asked Questions (FAQ)
Can leaked intimate images be completely removed from the internet?
Not always. Public visibility can be greatly reduced, but private/offline copies may remain.
Is StopNCII safe to use?
Yes. The content never leaves your device. Only a digital fingerprint is shared.
What if I don’t have the original image?
You can still report manually to platforms and search engines.
Should I pay someone threatening to leak my images?
No. Paying usually leads to more demands.
Is NCII illegal?
In many countries, yes. Laws vary, but it is increasingly criminalized worldwide.
📌 Call-to-Action
If this article helps even one person regain control, it has done its job.
- Share it responsibly
- Bookmark it for emergencies
- Talk about digital consent
- Support victims, not abusers
Because privacy is not a privilege.
It’s a right.

