(And what developers can do to stop them)
Important note for readers:
This article explains reverse engineering at a high, educational level—the why and how it works conceptually—not step-by-step instructions to illegally crack software. Reverse engineering has many legitimate uses: malware analysis, vulnerability research, interoperability, academic study, and defensive security. Always follow the law and the license terms in your country.

Reverse engineering has always lived in a strange gray zone.
On one side, it’s a core cybersecurity skill used by malware analysts, security researchers, and incident responders. On the other, it’s the same knowledge pirates use to bypass licenses, disable protections, and redistribute paid software for free.
And here’s the uncomfortable truth:
If software runs on your machine, it can be reverse engineered.
Not always easily. Not always cheaply. But eventually.
In this deep-dive, we’ll unpack how hackers crack software using reverse engineering, the mindset behind it, the tools and techniques (conceptually), and—most importantly—how modern software tries to defend itself.
This article is written for:
- Aspiring cybersecurity professionals
- Developers who want to protect their software
- Blue teamers learning attacker tradecraft
- Curious technologists who want to understand what’s really happening under the hood
Table of Contents
- What Is Reverse Engineering?
- Why Hackers Reverse Engineer Software
- How Software Becomes Crackable
- The Reverse Engineering Mindset
- Static Analysis (Without Running the Program)
- Dynamic Analysis (Watching Software While It Runs)
- Common Software Protection Mechanisms
- How Crackers Bypass Protections (Conceptual)
- Real-World Case Studies
- Why DRM Always Eventually Fails
- Reverse Engineering vs Malware Analysis
- Legal vs Illegal Reverse Engineering
- Defensive Reverse Engineering (Blue Team View)
- How Developers Can Make Cracking Harder
- Career Path: Reverse Engineering as a Skill
- The Future of Software Cracking
- Conclusion & Call to Action
- FAQ (Featured Snippet Optimized)
1. What Is Reverse Engineering?
Reverse engineering is the process of understanding how something works by analyzing it from the outside in—without access to the original source code or design documents.
In software, this means:
- Taking a compiled program (
.exe,.dll,.apk,.ipa) - Studying its structure, logic, and behavior
- Reconstructing how it works internally
Think of it like:
Getting a finished cake and figuring out the recipe by tasting, cutting, and inspecting it.
2. Why Hackers Reverse Engineer Software
Not all hackers reverse engineer for piracy—but piracy is where most people first hear about it.
Common Motivations
| Motivation | Purpose |
|---|---|
| Software cracking | Remove license checks |
| Game hacking | Cheats, mods, unlocks |
| Malware research | Understand malicious behavior |
| Vulnerability research | Find exploitable bugs |
| Interoperability | Make software work together |
| Academic learning | Learn low-level systems |
In cybersecurity, reverse engineering is defensive first:
- Analysts reverse malware
- Researchers audit binaries
- Blue teams investigate breaches
But attackers use the same skills.
3. How Software Becomes Crackable
Here’s the fundamental problem:
Software must reveal its secrets to run.
Even if:
- Code is obfuscated
- Strings are encrypted
- Logic is hidden
- Checks are scattered
Eventually:
- The CPU must execute instructions
- Memory must hold decrypted values
- Decisions must branch based on checks
That’s the opening hackers exploit.
4. The Reverse Engineering Mindset
Reverse engineering is not about tools—it’s about thinking like a machine.
Experienced reverse engineers ask:
- Where does the program decide “yes” or “no”?
- What happens when validation fails?
- What values change before success?
- What code executes only once?
They don’t brute force randomly.
They observe, hypothesize, test, repeat.
5. Static Analysis: Understanding Software Without Running It
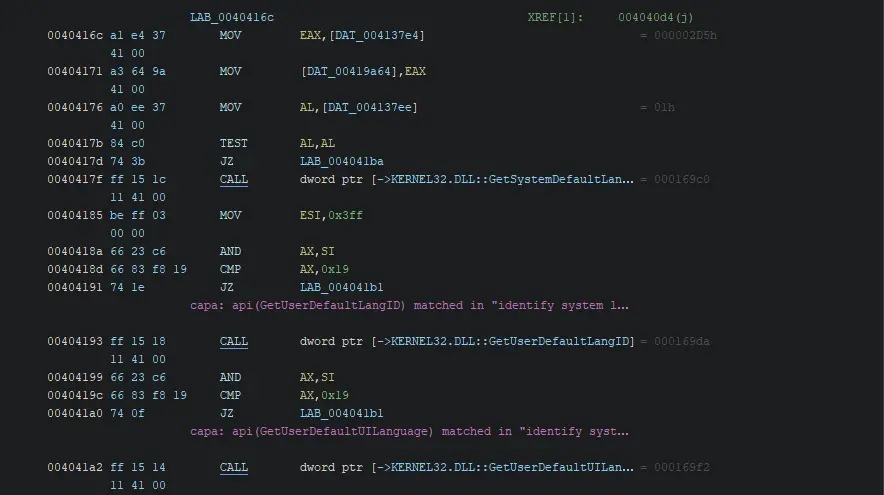
Static analysis means examining a program at rest.
What Analysts Look For
- Strings like:
- “Invalid license”
- “Trial expired”
- “Activation failed”
- Functions handling:
- Serial validation
- Network checks
- Hardware fingerprints
- Control flow:
- If/else logic around validation
Why Static Analysis Is Powerful
- No anti-debug triggers
- No execution risks
- Full overview of logic
Why It’s Hard
- Optimized compiler output
- No variable names
- Obfuscated control flow
This is where assembly language understanding becomes critical.
6. Dynamic Analysis: Watching Software While It Runs

Dynamic analysis observes a program in motion.
Instead of guessing, hackers watch:
- Which functions execute
- When checks occur
- How memory values change
Common Observations
- A variable flips from
0to1after validation - A function returns
falsewhen license fails - A network response controls access
Dynamic analysis answers one key question:
“What changes when the software thinks it’s activated?”
7. Common Software Protection Mechanisms
Modern software uses layered defenses.
Typical Protection Techniques
| Protection | Purpose |
|---|---|
| License keys | Gate access |
| Online activation | Central verification |
| Hardware binding | Lock to machine |
| Obfuscation | Hide logic |
| Packing | Compress/encrypt code |
| Integrity checks | Detect tampering |
| Anti-debug | Block analysis |
Each layer raises the cost, not the impossibility, of cracking.
8. How Crackers Bypass Protections (Conceptual Overview)
⚠️ No procedural steps here—only conceptual understanding.
Crackers don’t “break” cryptography.
They bypass logic.
Typical Bypass Strategies (High Level)
- Decision flipping
If validation returns “false,” force it to return “true.” - Check removal
Skip execution of protection routines entirely. - Environment simulation
Make software believe it’s licensed by emulating responses. - Patch-once approach
Modify binary so checks never execute again.
Key Insight
Protection fails at the decision point—not the algorithm.
9. Real-World Case Studies
Case Study 1: License Checks in Desktop Software
Many older desktop apps:
- Validate a serial locally
- Compare computed values
- Enable features based on a boolean flag
Once attackers find that flag, the rest is trivial.
Case Study 2: Game DRM Arms Race
Modern games use:
- Kernel-level drivers
- Virtualization detection
- Runtime encryption
Yet history shows:
Every major DRM has eventually been bypassed.
Not because crackers are smarter—but because the user controls the execution environment.
10. Why DRM Always Eventually Fails
DRM tries to enforce control after software is delivered.
That’s fundamentally unstable.
Reasons DRM Fails
- Runs on attacker-controlled hardware
- Must eventually decrypt itself
- Can be observed and modified
- Cannot fully trust the OS
This doesn’t mean DRM is useless—it buys time.
Time matters commercially.
11. Reverse Engineering vs Malware Analysis

The techniques are nearly identical.
Differences in Intent
| Area | Goal |
|---|---|
| Software cracking | Remove restrictions |
| Malware RE | Understand & neutralize |
| Security research | Discover vulnerabilities |
That’s why many top malware analysts started as reverse engineers.
12. Legal vs Illegal Reverse Engineering
This matters—especially if you want a career.
Generally Legal (Varies by Country)
- Malware analysis
- Security research
- Academic study
- Interoperability
- Debugging your own software
Often Illegal or Restricted
- Circumventing DRM
- Redistributing cracked software
- Violating license agreements
Intent + jurisdiction matters.
13. Defensive Reverse Engineering (Blue Team View)
Defenders reverse engineer to:
- Analyze malware payloads
- Extract indicators of compromise
- Understand attacker tooling
- Write detection rules
In fact, many SOC and IR roles require reverse engineering basics.
14. How Developers Can Make Cracking Harder (Not Impossible)
You can’t stop reverse engineering—but you can raise the cost.
Best Defensive Practices
- Server-side validation
- Short-lived licenses
- Frequent updates
- Behavior-based checks
- Runtime integrity verification
- Defense-in-depth
Strategic Truth
Your goal isn’t to stop hackers—it’s to outpace them.
15. Reverse Engineering as a Career Skill
Reverse engineering opens doors to:
- Malware analysis
- Threat intelligence
- Vulnerability research
- Exploit development
- Digital forensics
It’s one of the highest-paid niche skills in cybersecurity.
16. The Future of Software Cracking
AI will:
- Speed up pattern recognition
- Automate binary analysis
- Help classify protections
But AI also helps defenders.
The battle doesn’t end—it evolves.
Conclusion: Reverse Engineering Is Power—Use It Wisely
Reverse engineering isn’t magic.
It’s:
- Observation
- Patience
- Systems thinking
The same skill can:
- Protect millions of users
- Or enable mass piracy
Your intent defines the outcome.
If you’re learning reverse engineering:
- Do it ethically
- Do it legally
- Do it deeply
Because understanding how things break is how we learn to build them better.
Call to Action
If you want to go deeper:
- Study low-level systems
- Learn operating system internals
- Practice on legal labs
- Document what you learn
Reverse engineering isn’t about cracking software.
It’s about understanding reality beneath abstractions.
FAQ: Reverse Engineering & Software Cracking
❓ Is reverse engineering illegal?
Not inherently. It depends on intent, usage, and local laws.
❓ Do hackers really crack “any” software?
Given enough time and access, most client-side software can be bypassed.
❓ Is DRM useless?
No. DRM delays cracking and protects early revenue.
❓ Can reverse engineering help my cybersecurity career?
Absolutely. It’s a high-value, high-demand skill.
❓ Do I need to know assembly language?
Yes. At least basic understanding is essential.
❓ Is reverse engineering only for hackers?
No. Many defenders, analysts, and researchers use it daily.

